cómo espiar el celular de mi pareja gratis
En la era digital en la que vivimos, los teléfonos celulares se han convertido en una parte esencial de nuestras vidas. Se han convertido en una herramienta importante para la comunicación, el entretenimiento y el trabajo. Sin embargo, también pueden ser una fuente de preocupación y desconfianza, especialmente cuando se trata de relaciones de pareja. El deseo de saber qué está pasando en la vida de tu pareja puede llevarte a preguntarte si es posible espiar su celular de forma gratuita. En este artículo, exploraremos las diferentes formas en las que puedes espiar el celular de tu pareja de forma gratuita y si es ético hacerlo.
Antes de sumergirnos en cómo espiar el celular de tu pareja de forma gratuita, es importante tener en cuenta que la privacidad es un derecho humano fundamental. Todos merecemos tener nuestra privacidad respetada y violarla sin consentimiento es una violación de la ley. Espiar el celular de alguien sin su conocimiento o consentimiento puede ser considerado como una invasión a la privacidad y puede tener consecuencias legales. Por lo tanto, antes de tomar cualquier medida, es importante considerar si es ético y legal espiar el celular de tu pareja.
Una forma común de espiar el celular de tu pareja es a través de aplicaciones de monitoreo. Estas aplicaciones se pueden descargar en el celular de tu pareja y te permiten acceder a sus mensajes, llamadas, ubicación y más. Algunas de estas aplicaciones son gratuitas, pero la mayoría requieren una suscripción mensual o anual. Sin embargo, antes de descargar cualquier aplicación de este tipo, es importante asegurarse de que sea compatible con el sistema operativo del celular de tu pareja y que sea legal en tu país.
Una de las aplicaciones de monitoreo más populares y gratuitas es Spyic. Esta aplicación te permite monitorear el celular de tu pareja en tiempo real, incluyendo mensajes de texto, llamadas, ubicación y más. Sin embargo, para utilizarla, necesitarás tener acceso físico al celular de tu pareja para descargar la aplicación y configurarla. También es importante destacar que Spyic solo es compatible con dispositivos Android, por lo que no podrás utilizarla si tu pareja tiene un iPhone.
Otra aplicación gratuita de monitoreo es mSpy. Al igual que Spyic, esta aplicación requiere acceso físico al celular de tu pareja para su configuración. Una vez instalada, podrás acceder a mensajes, llamadas, ubicación y más. Además, mSpy ofrece una función de captura de pantalla remota, lo que te permite ver lo que tu pareja está haciendo en su celular en tiempo real. Sin embargo, al igual que Spyic, esta aplicación solo es compatible con dispositivos Android.
Si tu pareja tiene un iPhone, una opción gratuita es iCloud. Si conoces los detalles de inicio de sesión de su cuenta de iCloud, podrás acceder a sus mensajes, fotos, ubicación y más desde cualquier dispositivo a través de la aplicación de iCloud. Sin embargo, esta opción solo funciona si la función de copia de seguridad de iCloud está habilitada en el celular de tu pareja. Además, si tu pareja tiene habilitada la autenticación de dos factores en su cuenta de iCloud, necesitarás tener acceso físico a su celular para ver los códigos de verificación.
Otra forma de espiar el celular de tu pareja de forma gratuita es a través de la función de monitoreo de Google. Si tu pareja utiliza un dispositivo Android, puedes crear una cuenta de Google Family Link y vincularla a su celular. Esto te permitirá ver su ubicación en tiempo real, acceder a su historial de navegación en Chrome y bloquear aplicaciones en su celular. Sin embargo, esta opción solo funciona si tu pareja acepta ser monitoreado y si ambos utilizan dispositivos Android.
Además de las aplicaciones de monitoreo, también existen otras formas de espiar el celular de tu pareja de forma gratuita. Una de ellas es a través del uso de la tarjeta SIM. Si tienes acceso a la tarjeta SIM de tu pareja, puedes insertarla en tu celular y recibir todas las llamadas, mensajes y notificaciones que reciba tu pareja. Sin embargo, esta opción solo funciona si tu pareja utiliza una tarjeta SIM y si ambos utilizan el mismo operador de telefonía móvil.
Otra forma de espiar el celular de tu pareja es a través de los registros de llamadas y mensajes. Si compartes una cuenta telefónica con tu pareja, puedes acceder a los registros de llamadas y mensajes a través de la factura. Además, si conoces su número de teléfono y su proveedor de servicios, puedes solicitar los registros de la compañía de telefonía móvil. Sin embargo, esta opción solo te permitirá ver los números de teléfono y no el contenido de las llamadas o mensajes.
En resumen, existen varias formas de espiar el celular de tu pareja de forma gratuita, como a través de aplicaciones de monitoreo, la cuenta de iCloud, la función de monitoreo de Google y más. Sin embargo, es importante tener en cuenta que espiar el celular de tu pareja sin su conocimiento o consentimiento puede ser considerado una violación a su privacidad y puede tener consecuencias legales. Por lo tanto, antes de tomar cualquier medida, es importante considerar si es ético y legal hacerlo y tener una conversación abierta y honesta con tu pareja sobre tus preocupaciones.
how to recover hacked spotify account
Spotify is one of the most popular music streaming platforms in the world, with over 299 million active users as of December 2020. With a vast library of songs, podcasts, and other audio content, it has become an essential part of many people’s daily lives. However, with its popularity, the platform has also become a prime target for hackers. If you are reading this, chances are you or someone you know has fallen victim to a hacked Spotify account. In this article, we will guide you on how to recover a hacked Spotify account and ensure the safety of your personal information.
1. Identify the Signs of a Hacked Spotify Account
The first step in recovering a hacked Spotify account is to identify the signs of a breach. Some of the common signs of a hacked account include unauthorized changes to your account information, such as your password, email address, or payment details. You may also notice unfamiliar songs, playlists, or devices connected to your account. Furthermore, if you receive emails or notifications from Spotify about changes you did not make, it is a clear indication of a hacked account.
2. Change Your Password Immediately
If you suspect that your Spotify account has been hacked, the first thing you should do is change your password. This will prevent the hacker from accessing your account further and making any more unauthorized changes. It is recommended to use a strong and unique password, a combination of uppercase and lowercase letters, numbers, and special characters. Also, avoid using personal information that can be easily guessed by hackers, such as your name or birthdate.
3. Log Out of All Devices
Once you have changed your password, the next step is to log out of all devices connected to your Spotify account. This includes smartphones, tablets, laptops, and any other devices that you have used to access your account. To do this, go to your account settings and click on “Sign Out Everywhere.” This will ensure that the hacker is no longer able to access your account from any device.
4. Check Your Email for Suspicious Activity
Hackers often change the email associated with a hacked account to prevent the user from recovering it. Therefore, it is crucial to check your email account for any suspicious activity, such as emails from Spotify about changes to your account or password reset requests. If you find any such emails, take immediate action to secure your email account and contact Spotify’s customer support.
5. Contact Spotify’s Customer Support
If you are unable to access your account even after changing your password, it is best to contact Spotify’s customer support. You can do this by filling out a contact form on their website or reaching out to them via social media. Explain your situation and provide any evidence that proves your ownership of the account. Spotify’s customer support team will investigate the issue and help you recover your hacked account.
6. Enable Two-Factor Authentication
To ensure the security of your Spotify account, it is recommended to enable two-factor authentication (2FA). This adds an extra layer of protection to your account by requiring a code sent to your phone or email to log in. This way, even if a hacker manages to get hold of your password, they won’t be able to access your account without the code.
7. Keep an Eye on Your Account Activity
Once you have recovered your hacked account, it is essential to keep an eye on your account activity regularly. Spotify has a feature that allows you to view your account’s activity, such as logins, password changes, and connected devices. If you notice any suspicious activity, change your password immediately and contact Spotify’s customer support.
8. Secure Your Other Online Accounts
If your Spotify account has been hacked, it is possible that your other online accounts may also be at risk. This is because many people tend to use the same password for multiple accounts. Therefore, it is advisable to change your passwords for all other online accounts, especially those linked to your Spotify account, such as your email and social media accounts.



9. Be Wary of Phishing Scams
Phishing scams are one of the most common methods used by hackers to gain access to user accounts. These scams usually involve fake emails or websites that imitate legitimate companies, such as Spotify, to trick users into giving away their personal information. Therefore, it is crucial to be cautious and not click on any suspicious links or provide your personal information to anyone claiming to be from Spotify.
10. Use a Password Manager
One way to ensure the security of your online accounts is to use a password manager. This is a digital tool that stores all your passwords in one secure place. It generates strong and unique passwords for each of your accounts and allows you to access them with a master password. This way, you won’t have to remember multiple passwords, and your accounts will be less vulnerable to hacking attempts.
In conclusion, having your Spotify account hacked can be a stressful and frustrating experience. However, by following the steps mentioned above, you can recover your hacked account and ensure its security in the future. It is also essential to take preventive measures, such as enabling two-factor authentication and using a password manager, to protect your account from future hacking attempts. Lastly, remember to stay vigilant and report any suspicious activity to Spotify’s customer support.
all circles are similar true or false
When we think of circles, we often visualize a perfectly round shape with no angles or corners. This simple yet elegant shape has been studied and admired by mathematicians, scientists, and artists for centuries. But did you know that all circles are not only aesthetically pleasing, but also mathematically significant? In fact, one of the fundamental properties of circles is their similarity. In this article, we will explore the concept of similarity in circles and discover why it is a universally applicable concept.
First, let’s define what we mean by similarity. In mathematics, two objects are considered similar if they have the same shape, but not necessarily the same size. This means that the objects can be scaled up or down without changing their basic shape. For example, two circles with different radii are still considered similar if their shapes remain the same. This concept of similarity has been applied to various geometric shapes, but it is particularly relevant to circles.
To understand why all circles are similar, we must first look at the properties of circles. A circle is a shape with a constant radius, which is the distance from the center to any point on the circle’s circumference. This means that all points on the circumference of a circle are equidistant from the center. This property is known as the radius property of circles. Another important property of circles is that they have a constant circumference, which is the distance around the circle. This means that no matter how big or small a circle is, its circumference will always be the same.
Now, let’s consider two circles with different radii. If we were to draw a line connecting the centers of these circles and another line connecting any two points on their circumferences, we would notice something interesting. The two triangles formed by these lines are similar. This is because they have the same shape, but different sizes. In other words, the angles of these triangles are equal, but their lengths are proportional to the radii of their respective circles. This is known as the angle-angle similarity theorem.
This theorem can be applied to any two circles with different radii, no matter how big or small they are. This means that all circles are similar. This concept is not limited to just two circles, but can be extended to any number of circles. For example, let’s consider three circles with radii r1, r2, and r3. If we draw lines connecting their centers and any two points on their circumferences, we will get three similar triangles. This is known as the extended angle-angle similarity theorem.
The concept of similarity in circles has many applications in mathematics, science, and everyday life. One of the most significant applications is in geometry. Similarity is a fundamental concept in geometry, and it is used to solve various problems involving circles. For example, if we know the radius of one circle and the circumference of another, we can use the concept of similarity to find the radius of the second circle. This is known as the proportionality theorem.
Similarity in circles also has practical applications in the real world. In architecture and design, circles are used to create visually appealing structures, such as domes and arches. These structures are often constructed using similar shapes to achieve balance and symmetry. Similarly, in engineering, the concept of similarity in circles is used to design objects that have a specific shape but can be scaled up or down as needed. For instance, the wheels of a car are similar circles, but with different radii.
Apart from its mathematical and practical applications, the concept of similarity in circles also has a deep philosophical significance. It teaches us that no matter how different two objects may seem, they can still have a fundamental similarity. This can be applied to people, cultures, and societies. We may have different backgrounds, beliefs, and values, but at our core, we are all similar in our humanity.
The concept of similarity in circles has also been explored in various works of art and literature. In the famous novel “The Great Gatsby” by F. Scott Fitzgerald, the green light at the end of Daisy’s dock is described as a “minute and faraway” circle. This symbolizes not only the unattainable nature of Gatsby’s dream, but also the idea that everything in life is connected and similar in some way.
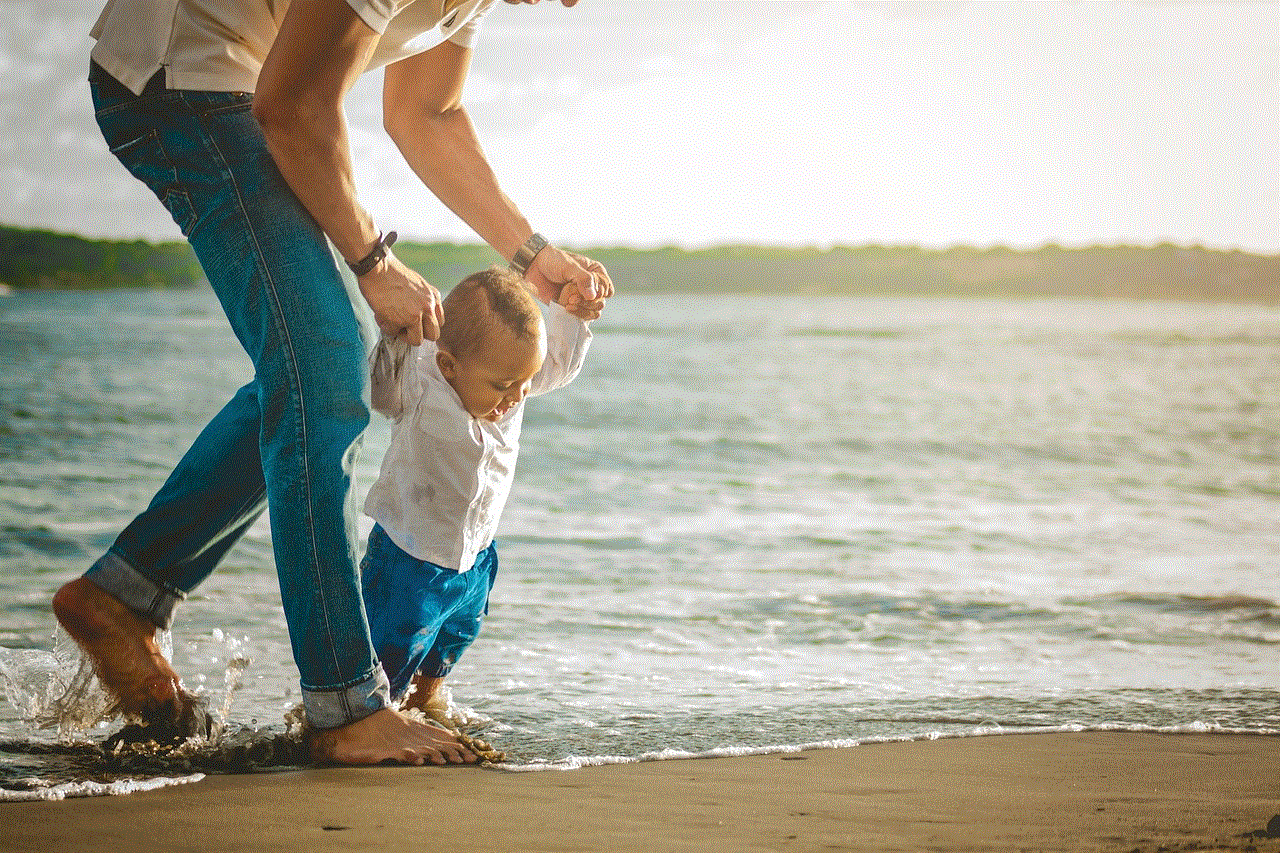
In conclusion, all circles are similar, and this is a fundamental property that has been studied and applied in various fields of study. From mathematics and science to art and philosophy, the concept of similarity in circles has far-reaching implications. It teaches us that no matter how different something may seem, there is always a fundamental similarity that connects us all. So the next time you see a circle, remember that it is not just a simple shape, but a powerful symbol of the universal concept of similarity.